GreatFire revealed that the popular Microsoft Outlook emailing service was subjected to a man-in-the-middle (MITM) attack in China.
This time the popular Outlook email service was allegedly hacked by Chinese authorities. The Outlook email service was not reachable in China over the weekend and according the to experts at the GreatFire organization, Chinese Government run a man-in-the-middle attack, exactly as it has already done in the past against many other web services. In December, the Gmail service has been blocked in China and also in that circumstance, the experts speculated that the Chinese Government used the China’s Great Firewall to interfere with the email service.
In a fist time, Chinese users suffered an anomalous outage for the Outlook service, the IMAP and SMTP protocols were not working on both on desktop and mobile email clients on Jan 17. GreatFire notes that the MitM attack only affected the email clients while web services outlook.com and live.com were not impacted.
“We have tested Outlook to verify the attack and have produced the same results. IMAP and SMTP for Outlook were under a MITM attack. Do note however that the web interfaces (https://outlook.com and https://login.live.com/ ) were not affected. The attack lasted for about a day and has now ceased.” reports a blog post published by GreatFire .
According to the GreatFire, the Man-in-the-Middle attack only affected the email clients and web interface of outlook.com website, meanwhile live.com were not affected.
“This form of attack is especially devious because the warning messages users receive from their email clients are much less noticeable than the warning messages delivered to modern browsers.” continues GreatFire.
GreatFire seems to have no doubts, the attack was operated by the work of the Cyberspace Administration of China which was earlier known as State Council Information Office and that is the principal Internet watchdog operated my the authorities.
The department directs, coordinates and supervises online content management and handles administrative approval of businesses related to online news reporting, it is an administrative office under the State Council.
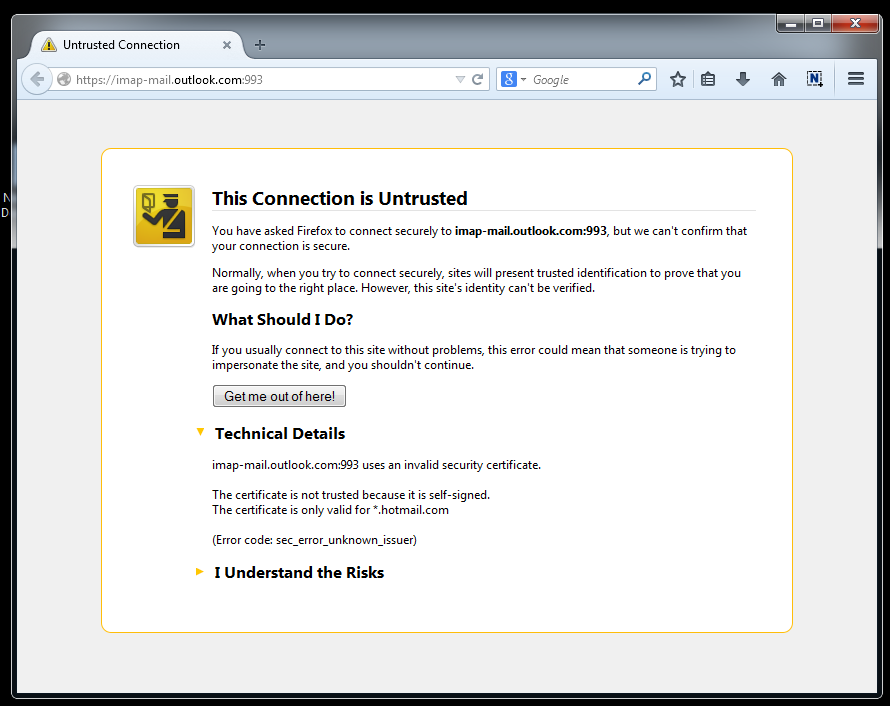
The experts at GreatFire conducted a series of tests trying to reproduce the issue by accessing Outlook using the same IMAP port for the email service in a browser and found that a the connection was established with a self-signed digital certificate.
“To reproduce the result in a Firefox browser, we first configured Firefox to allow access on port 993 which is the port used by IMAP. We then accessed https://imap-mail.outlook.com:993. We immediately received the warning message. As you can see, the certificate is self-signed, which is consistent with previous MITM attacks in China.”
GreatFire strongly suggests organizations, including Microsoft and Apple, to revoke digital certificates used in the attack:
“We have outlined CNNIC’s dubious history in a previous blog post. Given the dangerous nature of this attack on Outlook, we again strongly encourage organizations, including Microsoft and Apple, to immediately revoke trust for the CNNIC certificate authority.”
(Security Affairs – GreatFire, Outlook)
The post Chinese Government runs a MITM attack against Microsoft Outlook appeared first on Security Affairs.



 First Time in Dozen Years Major CyberSec Bills Become Law
First Time in Dozen Years Major CyberSec Bills Become Law